Learning Resources with Lantech: IT Security

Are Cybersecurity Risks Lurking in Your Business
Latest Posts
You get a request in an email. Do you action it?
I guess if you’re asked to transfer your life savings to someone you’ve never heard of, you’ll know it’s a scam. But what if everything looks okay? What if it seems to be from..
Creating an incident response plan - a how to guide
An incident response program is an essential part of the overall information security management program. Being able to identify and respond to security incidents will help you..
Information security policies: why they are important to your business
Outdated, incomplete, and absent information security policies continue to plague organisations of all sizes. This article provides an overview of information security policies..
What is cyber hygiene and what does it mean for your business?
Did you know that most Cybersecurity incidents in the workplace occur due to human error. Identifying ways to avoid human error is key to preventing data breaches and limiting..
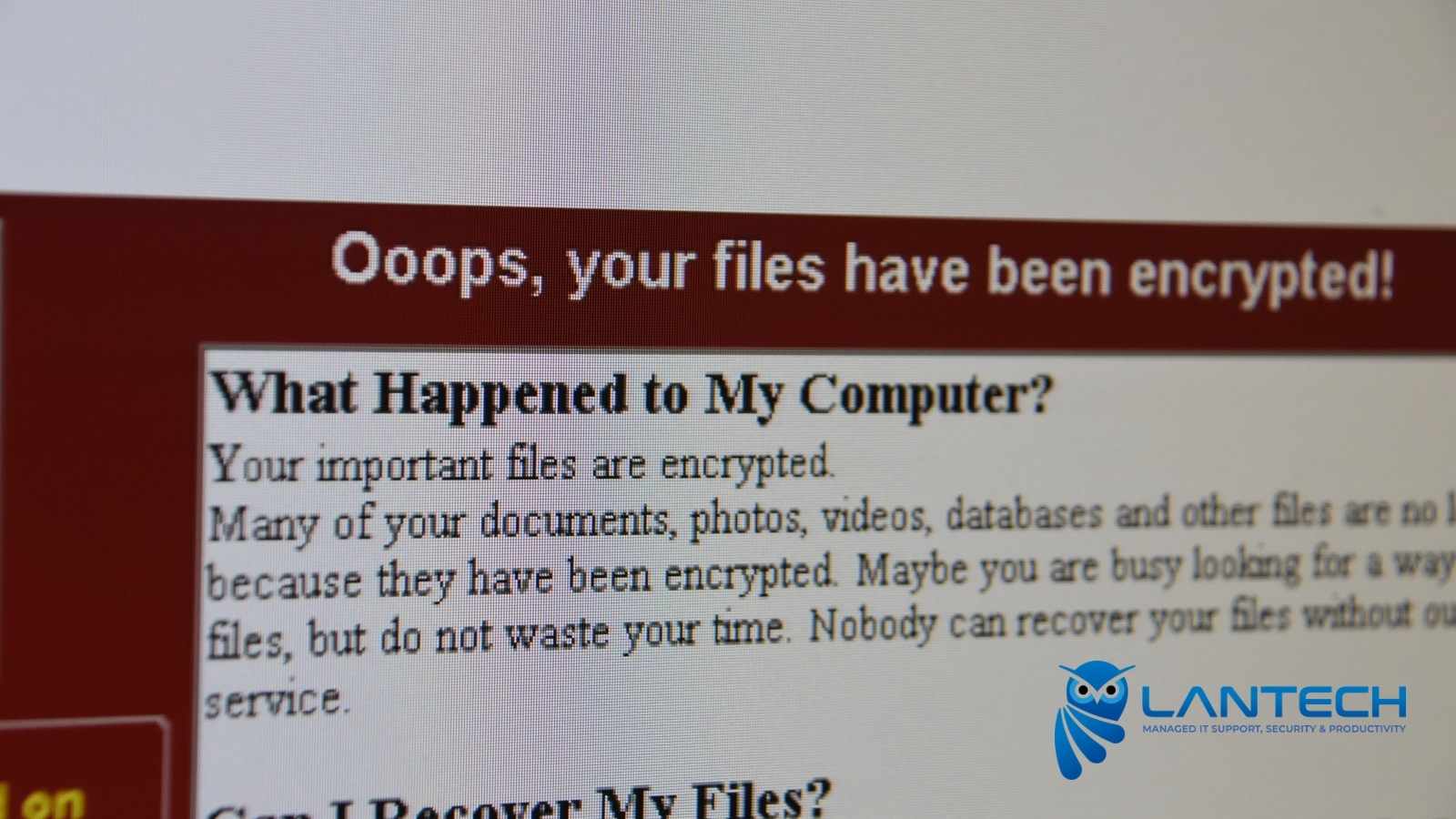
5 Quick Tips to protect your business from ransomware
Ransomware attacks are a major issue facing businesses, as Europe experienced a 234% surge in attacks in 2021. Small businesses are particularly vulnerable to ransomware schemes..
2FA & MFA: What’s the difference and Why You Need Them
Two-factor authentication and multi-factor authentication are essentially the same in that there is a requirement to use more than one factor for authentication. The subtle..
The risks of using public wi-fi and how to minimise them
The list of significant risks associated with using public a WiFi network is lengthy. Cybercriminals eavesdropping on unsecured networks steal sensitive data including account..
Subscribe
Get notified and receive a copy of our latest articles when they are published.